How the role of traditional CISO changes with the increase in Application related attacks?

With the ever-increasing number of cyber attacks and rapidly changing threat landscape, the role of CISO has been more critical for entire business operations and sustenance. CISOs face constant challenges regarding what tools and infrastructure security solutions to procure to secure their IT assets. They have built layers of defensive security solutions but in spite of all measures, they often face concerns with malicious hackers who find security vulnerabilities within their Application and often threaten them with some ransom.
CISOs are often not ready for these kinds of challenges and don’t know how to handle these hackers. Business reputation and continuity can be a huge stake in this situation. Enterprise needs to have a roadmap on how to develop and improve security maturity level. Security should be considered as philosophy and culture within the organization and should align their people, process and technology to achieve that.
Enterprise Strategy Group has nicely crafted Cyber-security Maturity Model using a scoring system to divide enterprises into three distinct segments in terms of their Cyber-security skills, resources, and technologies as: Basic, Progressing, and Advanced organizations. It provides analysis by focusing at four areas: Cyber-security philosophy, People, Process, and Technologies.
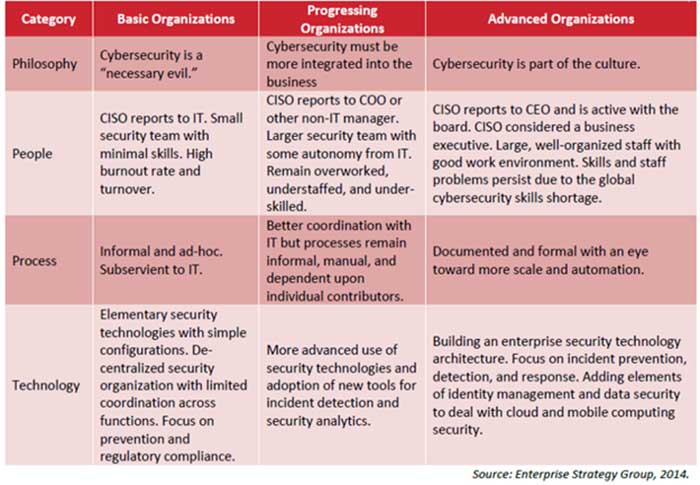
CISOs can use this model as a guideline to assess their current security posture, plan out a future roadmap and overcome shortcomings faced by other enterprises.
To improve the security posture of application security, CISO can take few initiatives. First is creating a coordinated vulnerability disclosure policy. Second is adopting bug bounty program for continuous security testing of application.
For Vulnerability disclosure policy, organizations can follow ISO/IEC 29147:2014 which provides guidelines for the disclosure of potential vulnerabilities in products and online services. Vulnerability disclosure policy acts as first point of communication for external security researchers to reach out organization’s security team to report security vulnerabilities they have discovered from organization’s internet facing digtial assets. It also defines scope, rules of engagement, disclosure policy which sets clear guidelines and expectations for security researchers.
Bug Bounty programs are effective means to incentivize security researchers to discover critical vulnerabilities in both internal and public facing applications. Enterprise can set rewards/ bounty scheme for every researchers who provide the first unique valid vulnerability submission. Bug bounty as application security strategy has already been successfully adopted by leading organizations such as Google, Facebook, Uber, Dropbox and came to a logical conclusion that embracing a crowd of allies will a create a level playing field against the crowd of adversaries.
The fundamental principle of testing is “more eyes to the application, more vulnerabilities could be found”. Websites and applications of enterprise are used by many users holding critical data. Using an army of security researchers or crowdsourced security researchers can bring diverse skill set and multiple scenarios to identify critical vulnerabilities. The key to stay ahead of malicious hackers is “Discover and fix these vulnerability as early as possible before malicious hackers could find”. This could be achieved by employing a large number of crowdsourced security researchers.
Aligning Security with Organization’s business goals
The key concern of CISOs is how to align security with organization’s business goals. It is essential to identify and map critical business application & IT infrastructure with context to business objectives. These critical business application needs continuous security penetration testing to identify security vulnerabilities and fix it early one. Bug-bounty platforms like SafeHats, help enterprises to create vulnerability disclosure policy for their public facing digital assets and provide a platform for external security researchers to report any kind of security issues if they find while using any of the enterprise’s digital assets. This also helps to streamline security incident management process. The platform manages the communication coordination between external researchers and internal security team. CISO must adapt to proactive approach in identifying vulnerabilities and stay ahead in security of their business assets.
Sandip Panda
CEO & Co-founder, InstaSafe
See What’s Next in Tech With the Fast Forward Newsletter
Tweets From @varindiamag
Nothing to see here - yet
When they Tweet, their Tweets will show up here.






























