CVEs Abound, But Not Enough to Secure the Enterprise

A recent article by Taylor Armerding of CSO Online explores the current state of the Common Vulnerabilities and Exposures (CVE) program managed by MITRE (read about the origins of CVE and MITRE here). He expands on the creeping belief that the CVE, the old–guard vulnerability “dictionary,” is falling behind and leaving security teams and technologies that rely on it open to risk. And although MITRE taking measures to close the gap - including dedicating more resources to vetting and assigning CVE identifiers to vulnerabilities the response among some experts is that these will not be enough to rectify the outdated model.
MITRE has certainly made strides to bolster the system, logging 6,592 new vulnerabilities with CVE IDs in the first half of 2017 alone - compare that to 6,431 CVE IDs logged in all of 2016. From January to June of this year, MITRE has published on average 1,133 new CVE IDs each month. That’s a 210 percent increase over the 536 new CVE IDs per month average of 2016!
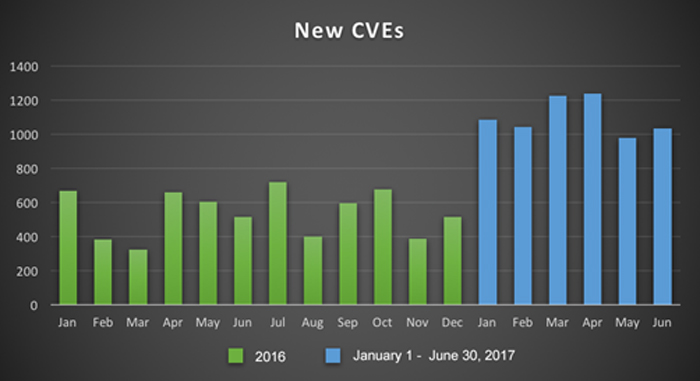
Source: MITRE
While increasing the number of vulnerabilities catalogued by the CVE system is generally good (many technologies use CVE IDs and some baseline vulnerability management programs rely on them almost entirely), it still doesn’t solve the issue of prioritization. Enterprises already have hundreds of thousands - even millions - of vulnerabilities in their organization. Assigning more CVE-IDs doesn’t directly lead to better security or even signify that more vulnerabilities exist today than in the past - it means more efforts are being dedicated to discovering, analyzing and cataloging vulnerabilities. Combined with a technology environment in a state of constant proliferation, this inevitably means more CVEs and vulnerabilities in general.
Currently, organizations are overwhelmed with too many vulnerability alerts to manage proficiently, so many of them are looking to advanced vulnerability management programs to help them better prioritize. In a recent report on vulnerability prioritization, Gartner analyst Craig Lawson points out that, “the lofty goal of ‘patch everything, all the time, everywhere’ is not only rarely fulfilled, it’s causing friction between IT security and IT operations.”
Focusing on the Right Vulnerabilities
Vulnerability teams, however, don’t need to patch everything all the time. The same report states that “only a small number of vulnerabilities go on to be xploited in real–world attacks.” This means vulnerability management programs should be structured to help teams zero in on the vulnerabilities most likely to be used in an attack - a much smaller portion than all CVEs.
Exploited vulnerabilities only make up a single digit of CVE-IDed vulnerabilities published each month. (The spike in March 2017 in the chart below represents the vulnerabilities leveraged in the EternalBlue exploit, famously used in WannaCry and NotPetya.) Vulnerabilities with a published proof–of–concept exploit (but inactive) represent a slightly larger portion, but still total less than 100 vulnerabilities published per month. With this information, security teams can:
- Focus resources on the vulnerabilities that are actually exploited in the wild first, as those are the ones that pose and imminent threat to the organization
- Employ mitigating controls (e.g., intrusion prevention systems, network segmentation, application controls, privileges management) to prevent lower–priority vulnerabilities from being exploited when those vulnerabilities can’t be patched in a reasonable period of time or when there is no patch available.
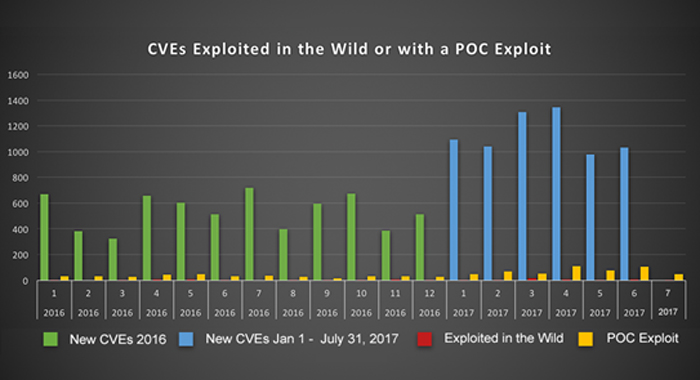
Source: MITRE and Skybox Research Lab
To help classify vulnerability risks even further, the Common Vulnerability Scoring System (CVSS) was developed over ten years ago to help organizations prioritize vulnerability remediation. A reasonable approach to vulnerability remediation in theory; however, implementation was never fully realized because of lack of vendor resources. So, only base CVSS scores have been used and have proved insufficient for prioritizing vulnerability remediation.
Unfortunately, this is the method many vulnerability management programs rely on, for all of its shortcomings: CVSS scores don’t consider the organization’s unique environment, the current threat landscape and other situational factors. For example, a vulnerability with a “high” CVSS score may not be exploitable in a particular network if the surrounding architecture and security policies provide sufficient defense. Similarly, a CVSS high–severity vulnerability on a low–value asset is less of a priority to fix than a CVSS medium–severity vulnerability on a business–critical asset.
Cyberattackers frequently leverage vulnerabilities carrying a medium severity CVSS score, perhaps because they know many vulnerability management programs are only capable of fixing CVSS critical vulnerabilities, never making it to the lower–ranking items on their to–do list.
The 2016 Verizon Data Breach Investigations Report also points out that successful exploits from the previous year targeted a large number of vulnerabilities with CVEs assigned more than five years ago - presumably, that organizations never got around to fixing.
How Skybox is Improving Vulnerability Prioritization
At the Skybox Research Lab, our team of analysts daily scour more than 30 security data sources and investigates more than 700,000 sites, including in the dark web. With this research, the Lab provides insight to active and available exploits, vulnerabilities being packaged in ransomware, exploit kits and other tools in used by various attackers.
The Research Lab has its own vulnerability catalog, which includes CVE vulnerabilities. But roughly 10 percent of this catalog also covers vulnerabilities with no CVE ID, including many on technologies in the IoT domain. This gives Skybox users a more complete scope of the vulnerabilities that could threaten their security. With the added intelligence of how vulnerabilities are being targeted in the wild, the Research Lab provides much needed context to improve prioritization in terms that put vulnerabilities posing an imminent threat at the top of your to–do list.
By focusing on vulnerabilities with active or known exploits as well as vulnerabilities that are exposed in your network (no mitigating controls in place), organizations can more effectively use existing resources to minimize the risk of a breach. However, this should be augmented with gradual risk reduction over time of the other vulnerabilities in the network, i.e. through mitigation or patching, which could turn into threats over time.
While both CVE and CVSS provide relevant information to vulnerability management programs and technology, they fall far short in terms of context that’s vital to understanding which vulnerabilities pose the most risk to you. It’s time to start seeing CVE and CVSS data as pieces of a much larger puzzle, one that requires advanced intelligence, analysis and automation to put together to help secure the enterprise.
See What’s Next in Tech With the Fast Forward Newsletter
Tweets From @varindiamag
Nothing to see here - yet
When they Tweet, their Tweets will show up here.






























